5 Must-Have Elements to Include in Your Security Awareness Program
When your aim is to change the culture of an organization, awareness isn’t enough
Nearly every security incident can be traced back to human error.
Data breaches, for example, often begin with a person being tricked into providing their access credentials to an attacker, from ‘fat-finger’ emails to the wrong recipient or from misconfigurations by system administrators.
Analyst group Gartner posits the potential of security awareness programs to yield more ROI than any other InfoSec investment. User behavior impacts security outcomes more than any technology, policy or process, it notes.
Nearly every security incident can be traced back to human error.
But as losses from incidents caused by human error grow unabated, are current approaches to awareness successfully making humans a harder target? In 2019, cyber attacks are mainstream news, awareness is heightened, but there is little evidence that behaviors are changing. The typical learning experience, delivered over a point-and-click video presentation, isn’t doing the job.
Over the past 12 months, Symantec has developed or commissioned several learning experiences that aim to progress from the cognitive aspects of learning (the acquisition of knowledge) to the behavioral (how and when that knowledge should be used) and procedural (putting the application of knowledge into habitual practice). We’re confident these activities are driving a measurable reduction in risk.
Each learning experience was developed according to the principles outlined below:
Empowering
Most awareness programs – ours included – are developed with a threat-based view of the world, trying to cover off all the human behaviors that attackers prey upon. We must take care however to ensure our education programs both raise and relieve anxiety about threats. Academics have demonstrated learners are more willing to embrace security policies and safer behaviours when made confident in their use of technology.
So, our program follows two key principles:
- For any given threat, the learning experience must instill confidence in how attainment of knowledge, skills or adherence to policy will help mitigate it.
- Every security event is a learning opportunity. There is insufficient evidence that deterrence, sanctions or coercion in isolation will drive policy compliance or safer habits. A user that makes an error or fails an assessment needs our help, not our scorn.
Actionable
Learners retain security-related information when advice is accompanied by a clear, practical action they can take to mitigate a given threat.
The most effective learning experiences embrace a ‘Tell, Show, Do, Apply’ approach. Take, for example, our approach to teaching password security to non-technical staff.
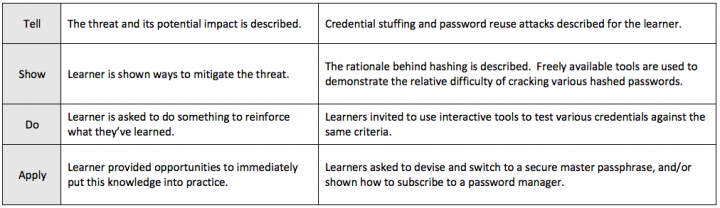
Engaging
Multiple empirical studies suggest an individual’s attitude and normative beliefs have a significant positive effect on intention to comply with security policies. People come to work with existing attitudes that play a ‘mediating’ role in whether they get value from an education program. They will only embrace learning they expect will be beneficial to them.
We’ve invested in promoting a ‘culture of security’ at Symantec. We enrolled our respected senior leaders in a highly visible campaign that set a new minimum standard for behaviours we expect from staff and suppliers. We stressed what’s at stake for us and our company.
Beyond this security advocacy, we ensure the mediums we use for training are enjoyable to interact with and relevant to the skills of the enrolled learners. Learning experiences must be engaging, easy to consume and concise.
We’ve invested in promoting a ‘culture of security’ at Symantec.
At Symantec we use gamification to drive engagement. Learners often ‘compete’ – either individually or in teams – to outrank peers or attain a higher status. A learning experience in which skill, creativity or application of knowledge is outwardly celebrated tends to trigger the pleasant sensation of peer validation. We love being seen to have won almost as much as we love winning.
My team publishes leaderboards for just about everything. We celebrate the teams that report the most phishing emails and the teams that outperform their peers at secure code tournaments. We celebrate the in-house researchers that compete to find and disclose the most security bugs in our products. We open up opportunities and forums for champions to spread their knowledge further inside and out of the organization.
Experiential
Learners are provably more likely to retain and apply advice if it is provided in the context of their daily work, and where opportunities are provided for strong, positive habits to form.
We ideally want to apply just-in-time training whenever a user’s interaction with a system introduces heightened risk. Consider the following examples, which relate to use of email.
| Threat | Threat Context | Learning Experience |
|---|---|---|
| Credential phishing | When a user opens an email from a new sender | o Phishing Readiness (simulations) |
| o Tools that provide indicators of trustworthiness (Symantec’s ‘Phishing Tacklebox’) | ||
| An email containing sensitive data is mistakenly sent to the wrong recipient | As a user is about to send an email | o Warning flags when an email recipient is outside the organization’s directory |
| o Tools that force users to classify documents and emails before they are sent (Symantec’s Information-Centric Tagging) |
There are many opportunities for providing short, teachable moments as a user engages with a given security technology. When a Symantec user is compromised by one of our monthly phishing assessments, for example, they are offered a short lesson on what ‘tells’ our team included in the lure that should have been identified, and a ‘just-in-time’ quiz to reinforce the learning outcome.
Role and Skill Relevant
Learning experiences must cater for levels of security expertise, which today sit across a large continuum.
Humans have a ‘psychological need’ to feel a sense of autonomy. Staff who perceive their behaviour as self-determined, to such a degree that they internalize policies, are more likely to comply with them.
At Symantec, software engineers and system administrators are provided additional training opportunities. Even when we train all staff in order to achieve a baseline of compliance, we offer multiple learning paths based on role and skill.
Dynamic and Responsive
Off-the-shelf security awareness learning experiences can struggle to keep pace with new threats and compliance requirements. Any learning experience that requires significant investment to update is not ideal.
At Symantec we chose to acquire learning platforms that enable us to build and edit bespoke learning experiences at speed. Where appropriate, we build web-based learning experiences from the ground up. We recently built and deployed a learning experience to several hundred engineers in response to a minor security incident in under a day.
Results-Driven
Our awareness program is focused on measurable outcomes.
While completion rates on training are an important metric, completion doesn’t guarantee a change in behaviours. So, we work with a variety of internal teams to measure our real-world impact on incidents, how and when they are reported, even the configuration choices and working habits of staff. We measure rates of recidivism among at-risk staff identified and trained under our phishing assessment program. We measure whether software engineers are getting sharper at identifying problematic classes of vulnerabilities.
We’re seeing strong signs of improvement.
Consecutive HR surveys of Symantec staff agree. In May 2019, 97% of surveyed staff expressed confidence in knowledge of their security responsibilities, 95% said they were provided the right advice to help protect their online interactions and 92% felt their team and immediate managers prioritize security appropriately.
In future blog posts, my team and I will detail the learning experiences we’ve rolled out and describe how each meet the above criteria.
If you’d like to hear more about Symantec’s Security Awareness Program, Brett Winterford will be speaking at the Gartner Security and Risk Management Conference in Sydney on Monday 19 August at 12:45pm.

Why MITRE ATT&CK Matters
This collaborative framework offers defenders a common language to talk about tactics and techniques to foil Advanced Persistent Threats










We encourage you to share your thoughts on your favorite social platform.