Case Study: The Dangerous Journey of a Fake WhatsApp App on OneDrive
Symantec recently discovered a new kind of malicious Android file hosted on a OneDrive account. Here’s what we learned and how you can take countermeasures
Over the last few years there has been a tremendous uptick in the creation and delivery of malicious Android apps for delivering malware, stealing confidential data, distributing spam advertisements for profit, and abusing mobile resources.
We recently encountered a different malicious Android file hosted on a OneDrive account. The Android file was named, “Gb whatsapp techmity.com hack.apk” i.e. “Fake WhatsApp”.
During the course of in-house research and intelligence collection activities, Symantec researchers discovered that Microsoft OneDrive was being used to distribute a “Fake WhatsApp” APK file.
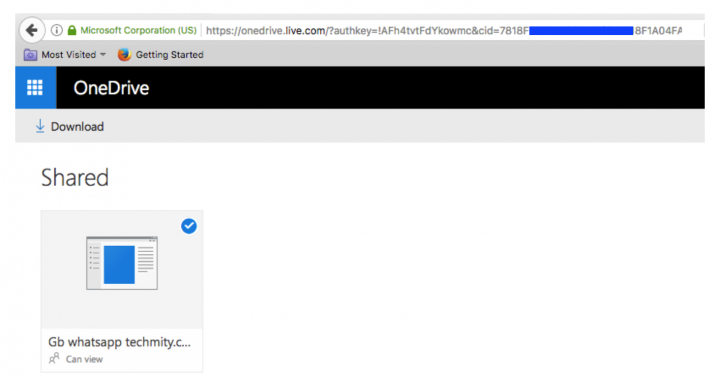
When the shared link on OneDrive was clicked, the user was prompted to download the ”Fake WhatsApp” Android package. Figure 2 shows a download of the “Fake WhatsApp” Android application.
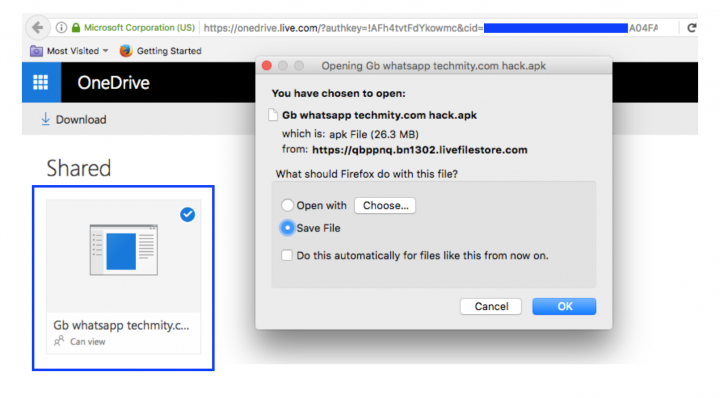
Let’s see what happens when the shared link was clicked.
The HTTP request was redirected by OneDrive to the LiveFileStore URL via a “Location” header. This shows that the Android application is not hosted directly on the OneDrive storage platform. Rather, it was hosted on the LiveFileStore platform.
The “livefilestore.com” is actually registered by Microsoft and used to store user-supplied content. This can be considered a content storage platform but it is not same as “1drv.ms”. If any file were to be uploaded by the user, it would be stored on the livefilestore.com and eventually mapped back to the 1drv.ms link.
(Request-Line) GET /v1.0/shares/<Truncated>/root/content HTTP/1.1
Host api.onedrive.com
User-Agent Mozilla/5.0 (Macintosh; Intel Mac OS X 10.11; rv:52.0) Gecko/20100101 Firefox/52.0
Accept text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language en-US,en;q=0.5
Accept-Encoding gzip, deflate, br
Referer https://onedrive.live.com/
Connection keep-alive
Upgrade-Insecure-Requests 1
(Status-Line) HTTP/1.1 302 Found
Via 1.1 DM5SCH102221312 (wls-colorado)
Content-Length 0
Location https://qbppnq.bn1302.livefilestore.com/<Truncated>611BSkrG8fbQ0zsp8fD5PgEuZ9kKlH5gONESEOxBKbPBI7nYO_I4HwTcTUebeYXSV-5Uz45k-qqW0OZ9uQ/Gb%20whatsapp%20techmity.com%20hack.apk
Server Microsoft-IIS/8.5
p3p CP="BUS CUR CONo FIN IVDo ONL OUR PHY SAMo TELo"
X-WLSPROXY DM5SCH102221312
X-MSNSERVER BN2BAPAE8784DE2
Strict-Transport-Security max-age=31536000; includeSubDomains
X-AsmVersion UNKNOWN; 21.2.0.0
X-AsmVersion-ProxyApp UNKNOWN; 21.2.0.0
x-msedge-ref Ref A: EE467E22CC15483C939B4702062508DC Ref B: PAOEDGE0313 Ref C: Sat Mar 25 23:58:00 2017 PST
Once the HTTP request is redirected to the LiveFileStore platform, the application is downloaded via the HTTP response header “Content-Disposition.”
(Request-Line) GET /<Truncated>XSV-5Uz45k-qqW0OZ9uQ/Gb%20whatsapp%20techmity.com%20hack.apk HTTP/1.1
Host qbppnq.bn1302.livefilestore.com
User-Agent Mozilla/5.0 (Macintosh; Intel Mac OS X 10.11; rv:52.0) Gecko/20100101 Firefox/52.0
Accept text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language en-US,en;q=0.5
Accept-Encoding gzip, deflate, br
Referer https://onedrive.live.com/
Connection keep-alive
Upgrade-Insecure-Requests 1
(Status-Line) HTTP/1.1 200 OK
Cache-Control public
Content-Length 27570277
Content-Type application/vnd.android.package-archive
Content-Location https://qbppnq.bn1302.livefilestore.com/y4m0ksvLOMFyTwEx1MMUu9uzAppzlyIXloVEDnijqxfp1QHemk1MGyDtvTFXBofR-ONLIq8QSk8kvAFHK3l0YXplQpXKsYQi4mVmGKLhL0nrDYdBFa6eg-v1EGec5dWr8OUMLApWC91pgA5AlYGo7uVbbp8EIXl_CJbuR07MufrmhIwnmSF2j46Ll4Jg-KGB_-F57tn0Anm6kDWi3Bs3gHn7w
Expires Sat, 24 Jun 2017 06:58:00 GMT
Last-Modified Sat, 04 Jun 2016 13:42:31 GMT
Accept-Ranges bytes
Etag aNzgxOEYxQTA0RkE5MjYxRSEyMTg5Ljg
Server Microsoft-IIS/8.5
p3p CP="BUS CUR CONo FIN IVDo ONL OUR PHY SAMo TELo"
X-MSNSERVER BN2BAP5CA124839
Strict-Transport-Security max-age=31536000; includeSubDomains
X-SqlDataOrigin S
CTag aYzo3ODE4RjFBMDRGQTkyNjFFITIxODkuMjU3
X-PreAuthInfo rv;poba;
Content-Disposition attachment; filename*=UTF-8''Gb%20whatsapp%20techmity.com%20hack.apk
X-Content-Type-Options nosniff
X-StreamOrigin X
X-AsmVersion UNKNOWN; 21.2.0.0
Generally, Hack Tool is considered malicious in nature because it is designed to perform some unverified operations that could impact the security state of the target device. The application was fetched and dissected for analysis. The application obtained the following set of permissions from the mobile device:
android.permission.READ_SYNC_SETTINGS (read sync settings)
com.huawei.android.launcher.permission.WRITE_SETTINGS (modify global system settings)
com.android.launcher.permission.UNINSTALL_SHORTCUT (Unknown permission from android reference)
android.permission.USE_CREDENTIALS (use the authentication credentials of an account)
android.permission.ACCESS_COARSE_LOCATION (coarse (network-based) location)
com.gbwhatsapp.permission.VOIP_CALL (Unknown permission from android reference)
android.permission.READ_SYNC_STATS (read sync statistics)
android.permission.RECEIVE_BOOT_COMPLETED (automatically start at boot)
android.permission.BLUETOOTH (create Bluetooth connections)
android.permission.CAMERA (take pictures and videos)
android.permission.INTERNET (full Internet access)
com.google.android.providers.gsf.permission.READ_GSERVICES (Unknown permission from android reference)
com.sec.android.provider.badge.permission.WRITE (Unknown permission from android reference)
android.permission.ACCESS_FINE_LOCATION (fine (GPS) location)
android.permission.SEND_SMS (send SMS messages)
com.android.launcher.permission.INSTALL_SHORTCUT (Unknown permission from android reference)
com.google.android.c2dm.permission.RECEIVE (Unknown permission from android reference)
android.permission.ACCESS_NETWORK_STATE (view network status)
android.permission.GET_TASKS (retrieve running applications)
android.permission.INSTALL_SHORTCUT (Unknown permission from android reference)
com.htc.launcher.permission.UPDATE_SHORTCUT (Unknown permission from android reference)
com.htc.launcher.permission.READ_SETTINGS (Unknown permission from android reference)
com.gbwhatsapp.permission.C2D_MESSAGE (C2DM permission.)
android.permission.WRITE_EXTERNAL_STORAGE (modify/delete SD card contents)
android.permission.RECEIVE_SMS (receive SMS)
android.permission.MANAGE_ACCOUNTS (manage the accounts list)
android.permission.WRITE_SYNC_SETTINGS (write sync settings)
android.permission.AUTHENTICATE_ACCOUNTS (act as an account authenticator)
android.permission.BROADCAST_STICKY (send sticky broadcast)
android.permission.WRITE_SETTINGS (modify global system settings)
android.permission.READ_PHONE_STATE (read phone state and identity)
com.gbwhatsapp.permission.BROADCAST (Unknown permission from android reference)
android.permission.WRITE_CONTACTS (write contact data)
android.permission.VIBRATE (control vibrator)
android.permission.READ_PROFILE (read the user's personal profile data)
com.huawei.android.launcher.permission.READ_SETTINGS (Unknown permission from android reference)
android.permission.WAKE_LOCK (prevent phone from sleeping)
android.permission.KILL_BACKGROUND_PROCESSES (kill background processes)
android.permission.ACCESS_WIFI_STATE (view Wi-Fi status)
com.gbwhatsapp.permission.MAPS_RECEIVE (Unknown permission from android reference)
com.huawei.android.launcher.permission.CHANGE_BADGE (Unknown permission from android reference)
android.permission.CHANGE_WIFI_STATE (change Wi-Fi status)
android.permission.RECORD_AUDIO (record audio)
android.permission.READ_CONTACTS (read contact data)
android.permission.MODIFY_AUDIO_SETTINGS (change your audio settings)
com.sonyericsson.home.permission.BROADCAST_BADGE (Unknown permission from android reference)
com.sec.android.provider.badge.permission.READ (Unknown permission from android reference)
android.permission.GET_ACCOUNTS (discover known accounts)
Permissions Obtained by the “Fake WhatsApp” Android Application
The following set of services were found to be configured:
com.gb.atnfas.WidgetService
com.gbwhatsapp.memory.dump.MemoryDumpUploadService
com.gbwhatsapp.messaging.MessageService
com.gbwhatsapp.ExternalMediaManager
com.gbwhatsapp.accountsync.AccountAuthenticatorService
com.gbwhatsapp.contact.sync.ContactsSyncAdapterService
com.gbwhatsapp.MediaTranscodeService
com.gbwhatsapp.LocationSharingService
com.gbwhatsapp.VoiceService
com.gbwhatsapp.notification.AndroidWear
com.gbwhatsapp.gdrive.GoogleDriveService
com.gbwhatsapp.VoiceMessagingService
com.gbwhatsapp.AlarmService
com.gbwhatsapp.gcm.experiment.PingCheckSchedulerService
com.gbwhatsapp.appwidget.WidgetService
com.gbwhatsapp.gcm.GcmListenerService
com.gbwhatsapp.gcm.InstanceIdListenerService
com.gbwhatsapp.gcm.RegistrationIntentService
com.gbwhatsapp.ContactChooserTargetService
com.gbwhatsapp.notification.DirectReplyService
Permissions Obtained by the “Fake WhatsApp” Android Application
Analysis shows that the application usually performs some unauthorized operations on end-user devices and it uses the name of a legitimate service provider.
Countermeasures
CloudSOC can detect this threat as shown below:
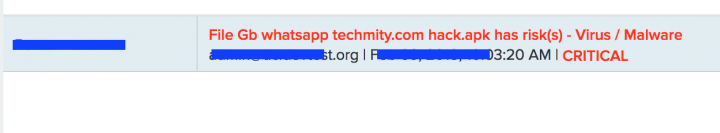
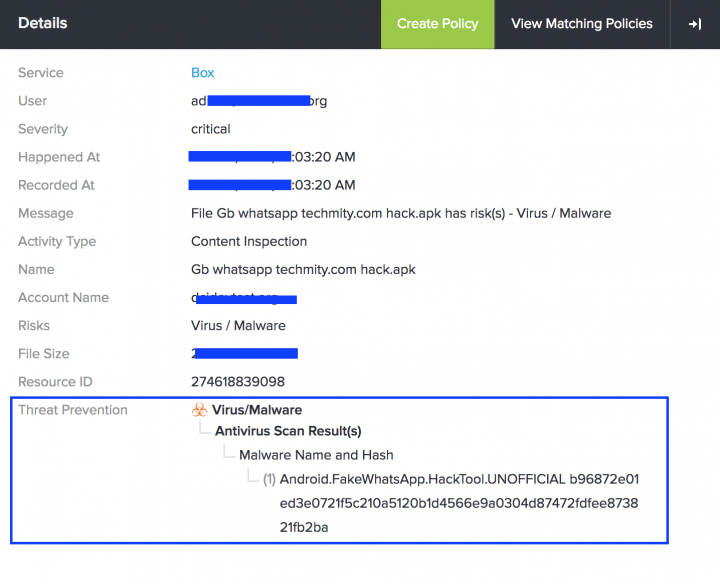
Some typical countermeasures to mitigate these types of attacks could include:
- Analysis and control of cloud application transactions with User Behavior Analytics (UBA). Symantec CloudSOC CASB inspects cloud application traffic and tracks how users interact with these apps. If the user behavior analytics observes abnormal or high risk user activity CloudSOC will increase the threat level for that user and policy controls will be triggered to alert, quarantine, or block activity from that user.
- Detect malicious files sitting in OneDrive via APIs and files in transactions with OneDrive.
Symantec’s advanced malware analysis engine, along with CloudSOC, will scan files in cloud applications to detect, quarantine, or block malicious files.
Appendix
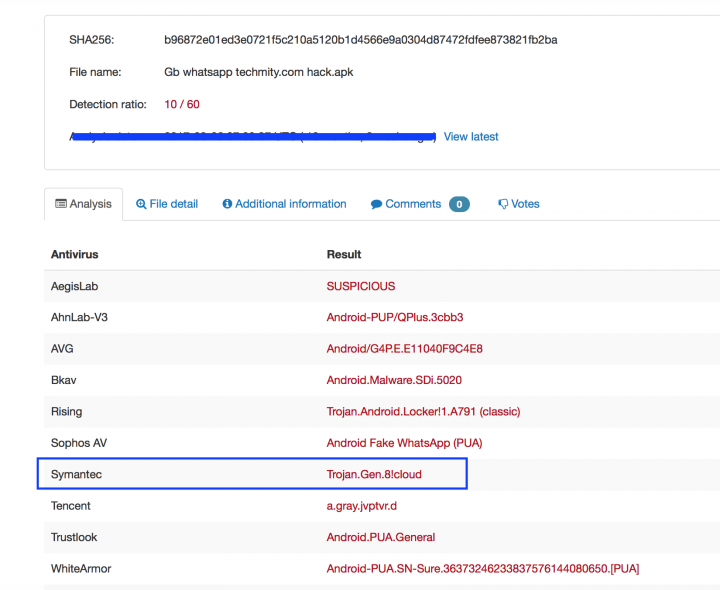
The virus total treat this file as suspicious as well as shown below. Symantec flagged the detect as “Trojan.Gen.8lCloud”










We encourage you to share your thoughts on your favorite social platform.