Text-Based COVID-19 Spam Wants Your Information, Money
Symantec’s Email Threat Isolation stops spammers as they continue to take advantage of coronavirus pandemic.
This is a follow-up to our previous blog on COVID-19 related spam campaigns. This blog will share some insight on the latest wave of COVID-19 themed spam campaigns and how Email Threat Isolation (ETI) from Symantec stops these emails from accomplishing their goals.
Symantec has continued to observe numerous malicious email campaigns taking advantage of the global panic surrounding the coronavirus outbreak. While we previously discussed malspam (malware bearing) emails, now a wave of text-based spam campaigns have emerged. These emails do not contain any malicious attachments and instead rely on what is written in the email to trick users into handing over information or money.
Change is the only constant
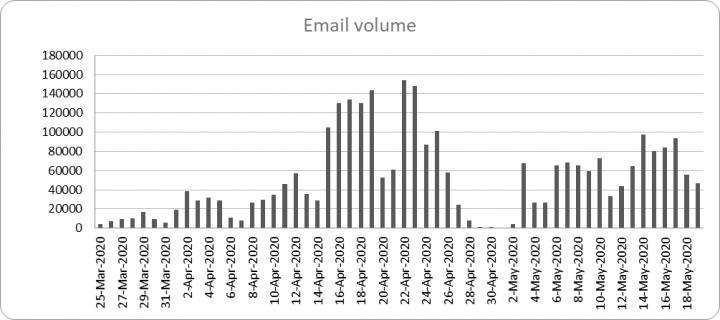
According to Symantec telemetry, as well as COVID-19 related phishing and malspam campaigns, spammers are increasingly using text-based campaigns. One reason for this is that it is comparatively cheaper and easier than phishing and malspam campaigns as there is no need for compromised domains or malware. The most abused vanity TLDs used in these campaigns are .xyz, .top, and .site.
These text-based spam campaigns include the following types of scams:
- Business proposition emails from small to medium-sized manufacturing factories offering to sell medical equipment like surgical face masks, personal protective equipment (PPE) kits, sanitizers, and ventilators
- Emails from generous donors claiming to be giving away large sums of money to those in need
- Lottery scam emails
- Emails asking for donations from individuals via cryptocurrency or gift cards
Symantec Email Threat Isolation
One of the best solutions or defense mechanisms provided by Symantec to its customers is Email Threat Isolation (ETI). ETI technology checks emails and attachments for phishing URLs or malicious content hosted on them. This technology de-risks the threat scenario by providing an extra layer of protection that allows users to safely browse unknown or shady websites, without risk of malware infection or credential theft. ETI is offered within the Symantec Email Security.cloud and Symantec Messaging Gateway solutions, and also as a standalone product that works with email security solutions from other vendors.
Phishing emails disguised as COVID-19 reports
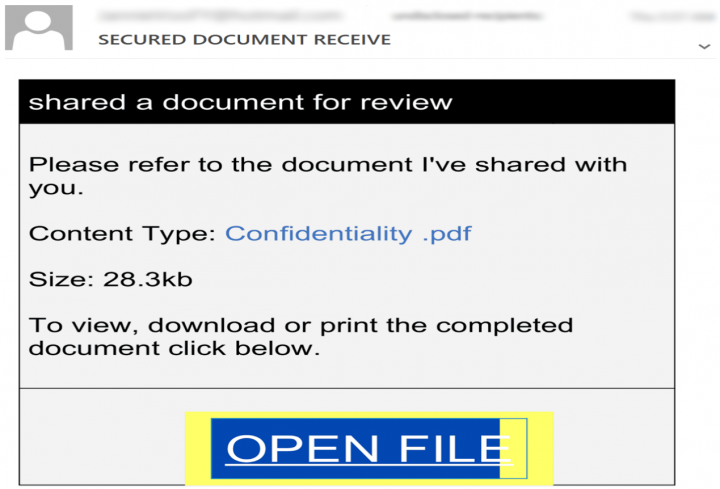
Phishing emails masquerading as COVID-19 funding reports are being spread in spam campaigns. These emails try their best to trick recipients into clicking on links that lead to phishing web pages designed to steal credentials. Threat actors have designed convincing email templates that appear to come from reputable file-sharing/storage services and use them for their phishing campaigns. An example of this can be seen in Figure 2. The email content is kept short and mentions that a confidential document has been shared with the email recipient. In order to view the “Confidentiality.pdf” file, the user needs to click on “OPEN FILE”, beneath which a recently registered domain is used to form a phishing URL:
https://[REMOVED]covid.com/
The phishing URL opens as a legitimate looking login page requesting the user to enter credentials.
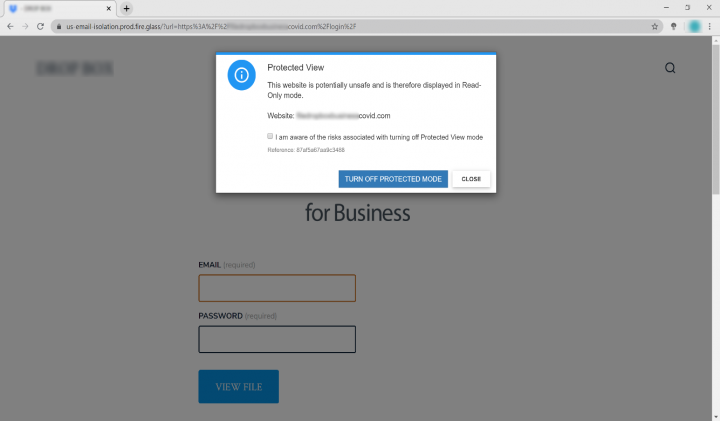
In Figure 3, Email Threat Isolation (ETI) alerts the user that the web page is potentially unsafe to visit and automatically enables the protected view with read-only mode. This helps to safeguard the user’s credentials or confidential information from being compromised.
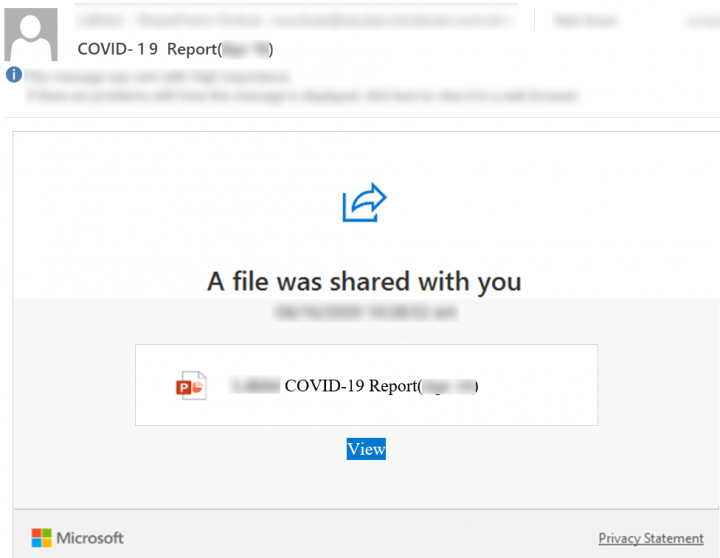
In Figure 4, a bogus email template is used to tell the recipient that a COVID-19 report file has been shared with them. When the “View” button is clicked, the user is brought to a phishing web page constructed with the help of a compromised domain:
https://[REMOVED]/ssl/?@=
Business proposition emails offering medical equipment
These emails claim to come from small to medium-sized manufacturing firms, offering for sale a variety of medical equipment. The email templates used are kept simple and direct. As with many of these scam emails, there are often grammar, spelling, and punctuation errors present.
In Figure 5, the threat actor provides a list of medical equipment specifying the type of respirators and masks available for purchase. The email also mentions that special chartered shipping services are available for VIP clients and provides shipping details.
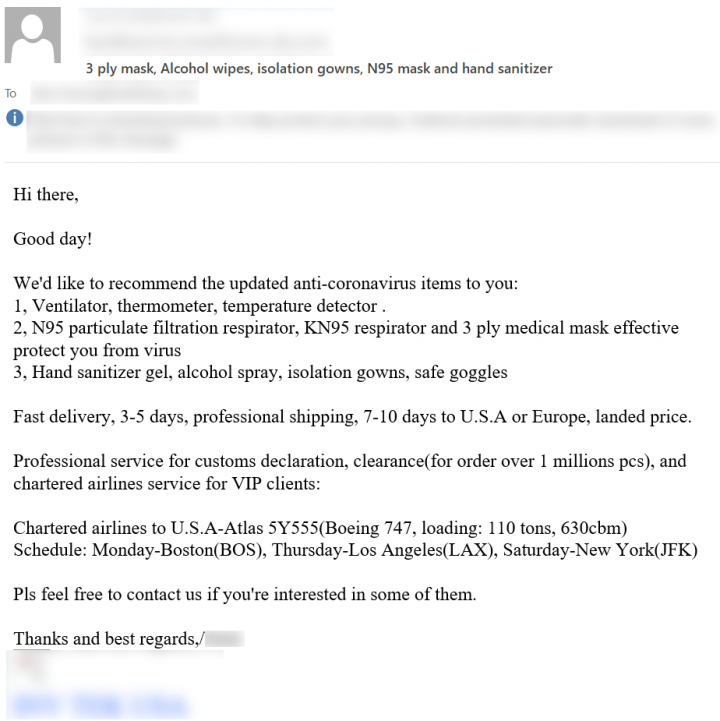
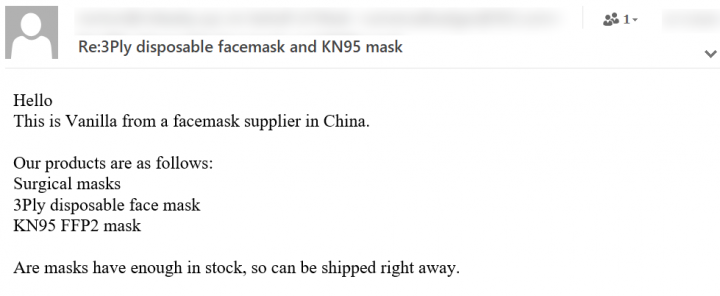
In Figure 6, the threat actor poses as a supplier from China keen to ship various types of face masks to different parts of the world with abundant stock ready to ship.
Generous donors offer donations
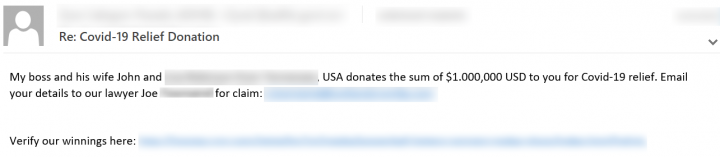
This is another variation of the infamous advance fee scam. These emails are generally kept short and try to attract victims by offering generous monetary donations. In Figure 7, a generous wealthy couple is supposedly donating money for the Covid-19 relief effort. The email asks the recipient to provide personal details to a lawyer in order to claim the money.
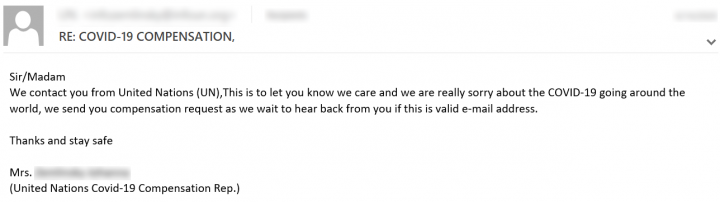
The email shown in Figure 8 is supposedly from the United Nations, in relation to COVID-19 relief. The email asks the recipient to verify their email address, which will then allow the sender to begin a conversation with the user and begin their scam. The subject line of this email starts with “Re:”, a tactic used to trick the recipient into thinking the message is a continuation of previous correspondence.
Lottery scam emails
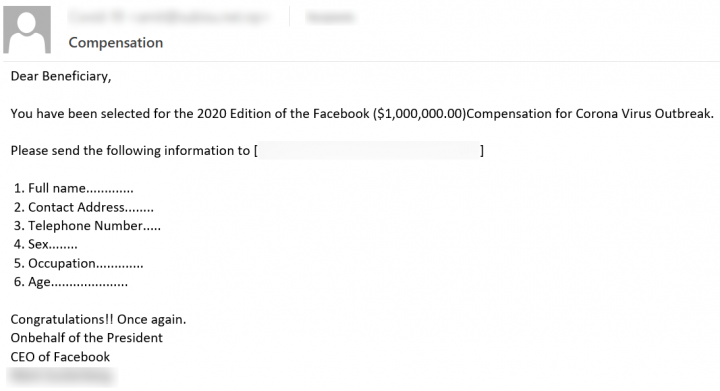
These emails are themed as notification emails notifying the user they have been selected in a lottery to receive coronavirus compensation. In Figure 9, one of these emails asks the user to provide personal information before applying for their share of $1,000,000.
Requesting donations via cryptocurrency
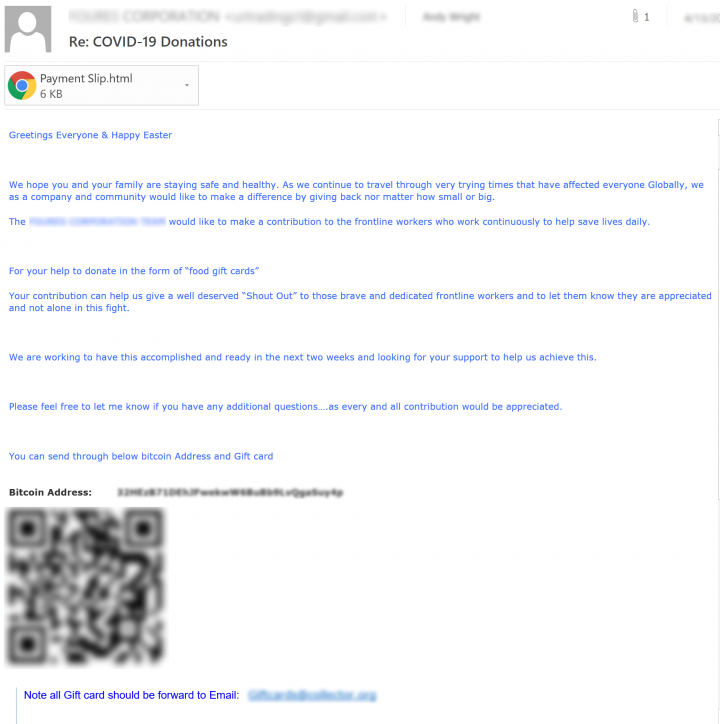
These emails leverage cryptocurrencies and QR codes. The email shown in Figure 10 presents the recipient with a Bitcoin wallet address and a QR code to supposedly donate money or “food gift cards” to help with the coronavirus pandemic relief effort. Scanning the QR code brings up the same Bitcoin wallet listed in the email text. The email also lists an email address where all gift cards should be forwarded to.
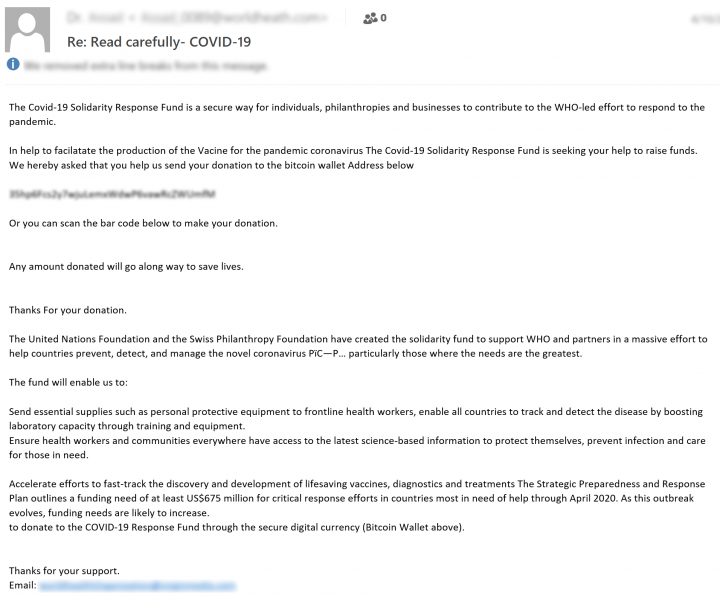
In Figure 11, the threat actor poses as a doctor and urges recipients to donate funds towards the COVID-19 Solidarity Response Fund, which will supposedly help with the production of a COVID-19 vaccine. Donations are requested to be paid to the provided Bitcoin wallet address.
Snowshoe campaigns
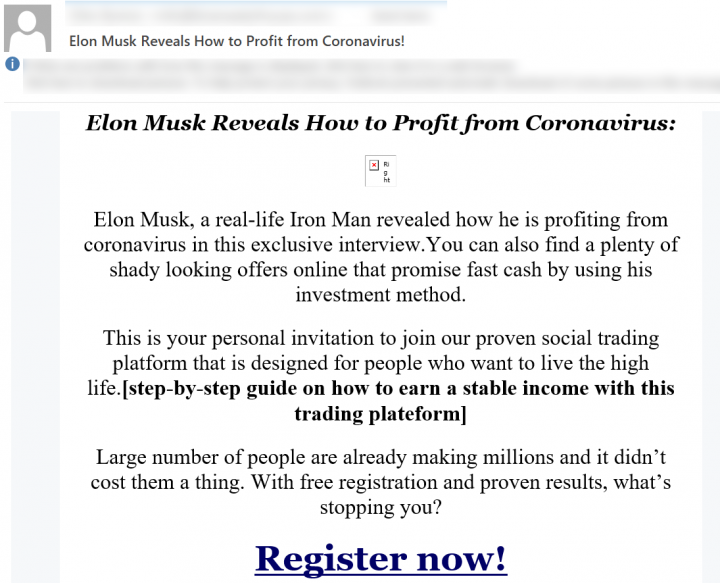
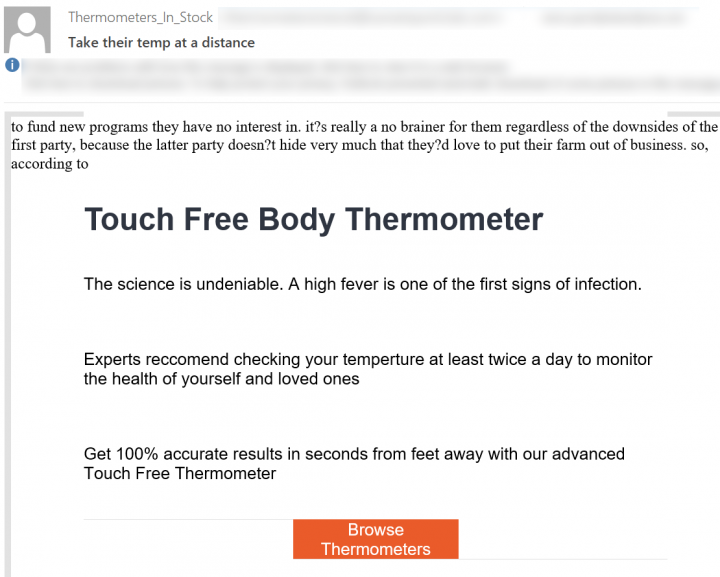
Snowshoe campaigns continue to be a firm favorite for spammers. These campaigns appear with heavy randomization in header fields to avoid detection. Snowshoe campaigns come in large batches in a short period of time. Along with heavy randomization of email features, these runs also use a myriad of topics and themes. In addition, these emails are distributed with a variety of originating IP addresses, domains with different gTLDs, and heavy obfuscation to avoid detection. In Figures 12 and 13, threat actors have made use of current affairs and designed their email templates accordingly. These include themes like “Elon Musk Reveals How to Profit from Coronavirus” and the promotion of a “Touch Free Body Thermometer.” Ultimately, the URLs hyperlinked beneath the words “Register now!” and “Browse Thermometers” contain newly registered spam domains.
Protection against COVID-19 themed messages
Predictive filtering systems focused on URL and other email features are deployed in timely intervals to catch changes in the rapidly changing email threat landscape. With the help of predictive filtering systems, threats that use email as a medium are filtered or blocked before they cause menace. This approach has also proved beneficial to detect the variation in these types of attacks and filter them down in terms of volume or scale.
Mitigation steps
- Email users are requested to thoroughly check emails and if deemed suspicious, please report it to Symantec.
- Question any emails requesting actions that seem unusual or aren't following normal procedures.
- Analyze potential threats using analytics technologies that can pick up on the subtle differences between clean and infected emails and identify indicators of compromise.
- Conduct end-user awareness training to raise overall awareness of phishing among employees.
Defense mechanisms
At Symantec, response teams strive hard to protect our valuable customers by introducing new defense mechanisms against such challenging attacks. An array of defense mechanisms is deployed in different layers at .cloud and Symantec Mail gateway level to block similar attacks.
- Symantec Email Security.cloud Data Protection: Provides granular control to identify suspicious messages based on various indicators and helps to flag messages that are coming from outside the organization.
- Symantec Data Loss Prevention: Helps combat the data theft scenario by seamlessly integrating with our Email Security solutions.
- Email threat isolation (ETI) from Symantec: Checks emails and attachments for phishing URLs or malicious content hosted on them. This technology de-risks the threat scenario by providing an extra layer of protection that allows users to safely browse unknown or shady websites, without risk of malware infection or credential theft. Symantec Email Threat Isolation is offered within the Symantec Email Security.cloud and Symantec Messaging Gateway solutions, and also as a standalone product that works with other vendors' email security solutions.
COVID-19 Outbreak Prompts Opportunistic Wave of Malicious Email Campaigns
Spammers, scammers, and other threat actors quick to take advantage of global panic surrounding coronavirus outbreak









We encourage you to share your thoughts on your favorite social platform.