Threat Landscape Trends – Q3 2020
A look at the cyber security trends from the third quarter of 2020.
We took a look through telemetry from our vast range of data sources and selected some of the trends that stood out from July, August, and September 2020
From significant increases in Emotet and Cobalt Strike activity to a spike in the number of server vulnerability exploit attempts, let’s take a quick look at the trends that shaped the cyber security threat landscape in the third quarter of 2020.
Malware steadily increases
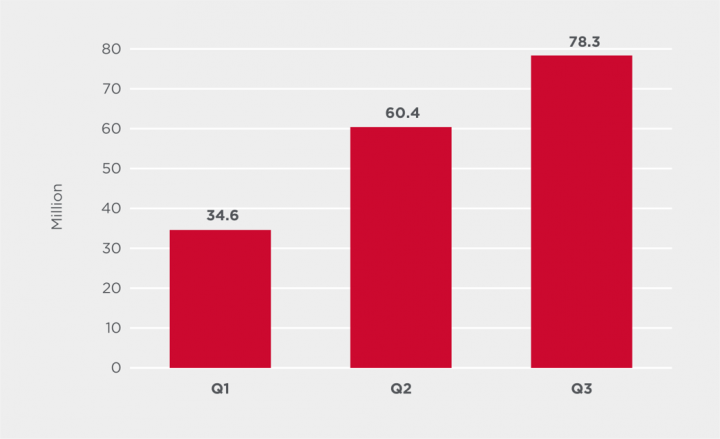
Malware attacks have continued to increase quarter over quarter in 2020. In July, August, and September, Symantec, a division of Broadcom (NASDAQ: AVGO), blocked over 78 million malware infection attempts, which represents an almost 30% increase over Q2 and a 127% increase over the number blocked in Q1. The increase in activity may have been spurred by many countries exiting COVID-19 lockdowns, with a resurgence in business activity presenting more opportunities for cyber criminals.
Downloaders
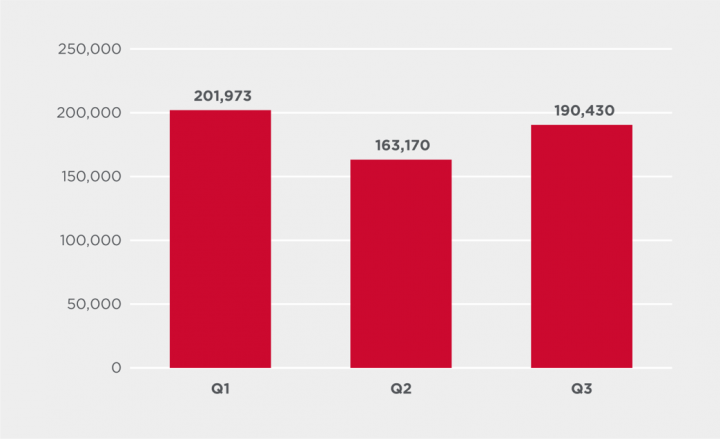
Malware that downloads files, which are often malicious, saw an increase in Q3. Symantec blocked 17% more of these threats in Q3 than in Q2.
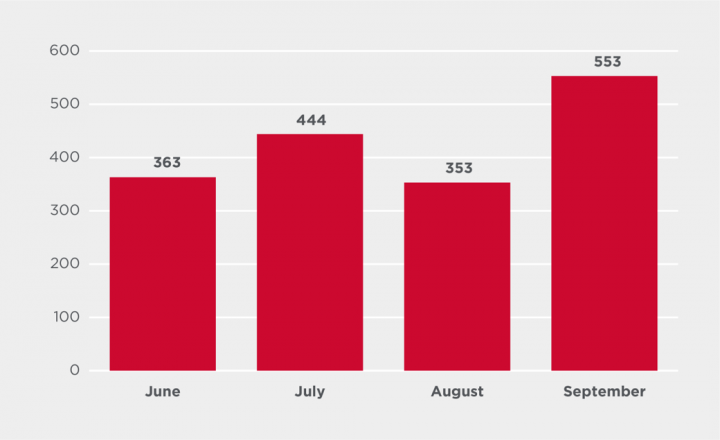
Cobalt Strike by month
Attacks involving the use of the multipurpose commodity malware Cobalt Strike (Backdoor.Cobalt), have continued to increase. Detections of attacks involving the use of this threat increased 57% from August to September alone.
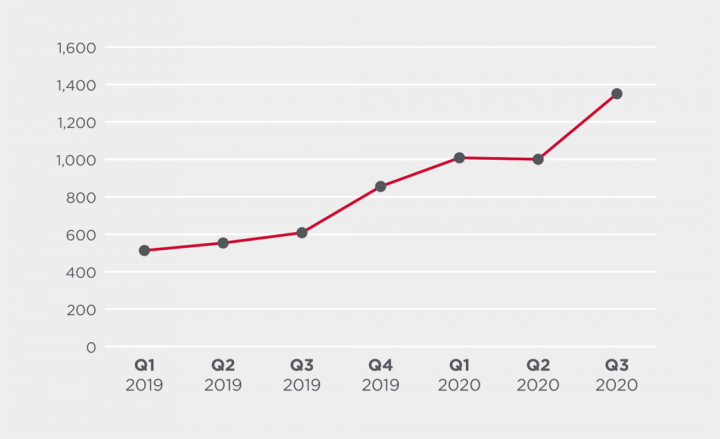
Cobalt Strike by quarter
The quarter on quarter trend is even more alarming, with a 163% increase seen when comparing Q1 2019 to Q3 2020. In many cases, Cobalt Strike is blocked by other detection technologies and signatures, meaning the true number of attacks involving this malware may be significantly higher.
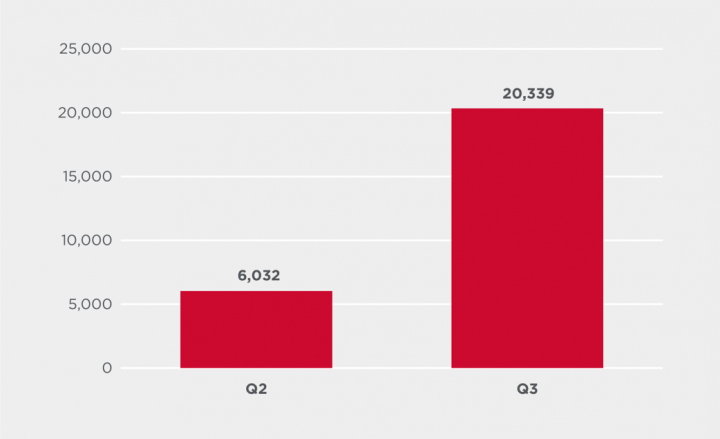
Lokibot by quarter
The Lokibot information-stealing malware (Infostealer.Lokibot) saw a 237% increase in activity from Q2 to Q3 2020. Lokibot is one of today’s most prevalent information-stealing threats and is often distributed via spam campaigns.
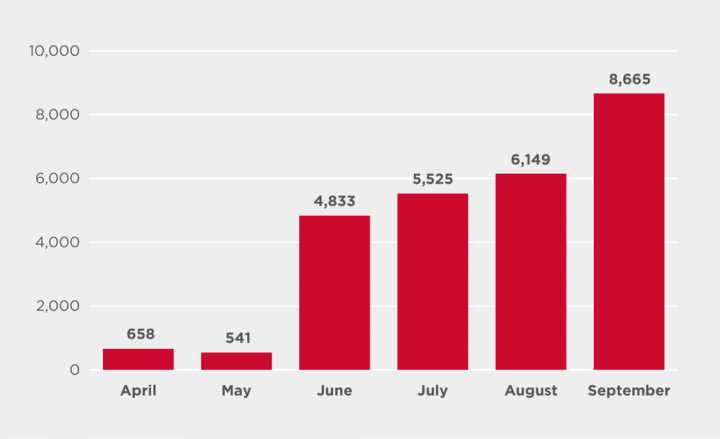
Lokibot by month
Blocked Lokibot attacks in September reached the highest number seen since June 2019.
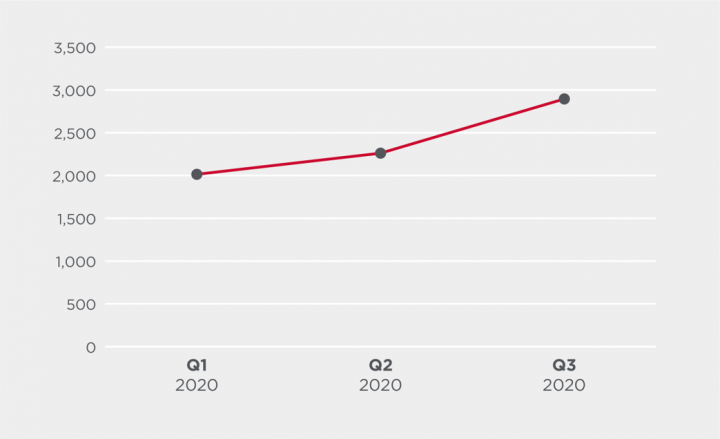
Emotet by quarter
As predicted towards the end of June, after over a year of subdued activity, the Emotet botnet (Trojan.Emotet), a known malware distribution platform, has returned in Q3. Following a dramatic drop in activity in Q2 2019 the malware looks to be steadily ramping up activity, with the number of blocked infection attempts in Q3 up 44% over that of Q1. The vast majority of Emotet infection attempts are blocked by email protection products, meaning antivirus detections are a small, representative sample of blocked Emotet activity.
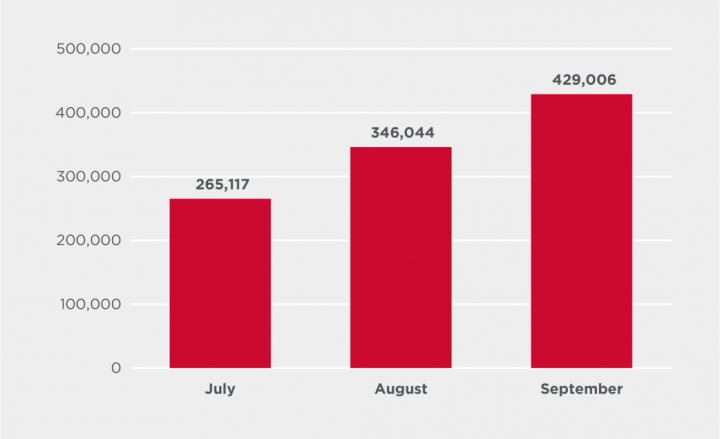
Emotet by month
Looking at the numbers by month, there was a significant jump in activity from June to September, equating to a 353% increase. The vast majority of these blocked Emotet attacks occurred in the U.S. Symantec observed and blocked an Emotet spam campaign in September which was using COVID-19 themed lures. This campaign contributed to the surge in activity seen in September. For additional information on Emotet, read our blog:
The Evolution of Emotet: From Banking Trojan to Threat Distributor

COVID-19 related spam
Spam emails using COVID-19 themed lures have increased month-on-month in Q3, with a roughly 27% increase in the number of these emails blocked by Symantec each month. As mentioned, Symantec observed and blocked an Emotet spam campaign in September which was using COVID-19 themed lures.
Phishing
In Q3, the number of phishing attempts blocked by Symantec’s Intrusion Prevention System (IPS) technology increased 25% over the previous quarter, and almost doubled (97%) over numbers from Q1 2020.
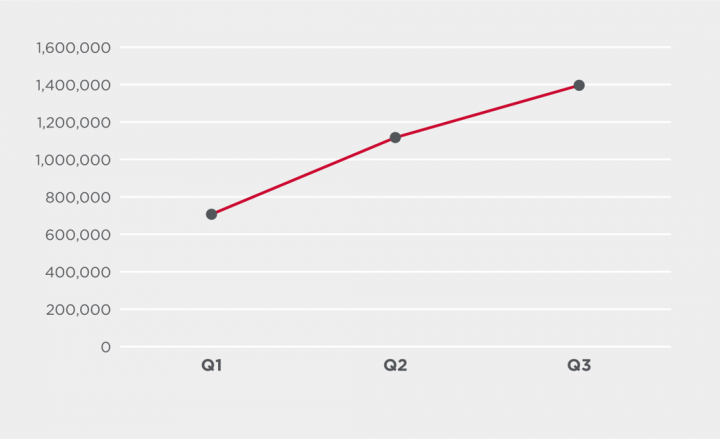
Server vulnerabilities
The number of server vulnerability exploit attempts blocked by Symantec IPS technology in Q3 increased by 77% over the previous quarter. This increase in exploit attempts follows a series of critical server vulnerability disclosures, such as the “Zerologon” flaw in Windows Server (CVE-2020-1472) and a vulnerability in Pulse Secure VPN servers (CVE-2019-11510). These types of vulnerabilities are tempting for hackers as they can offer access to enterprise servers and all the sensitive data stored there. Servers are also an ideal platform for launching further attacks.
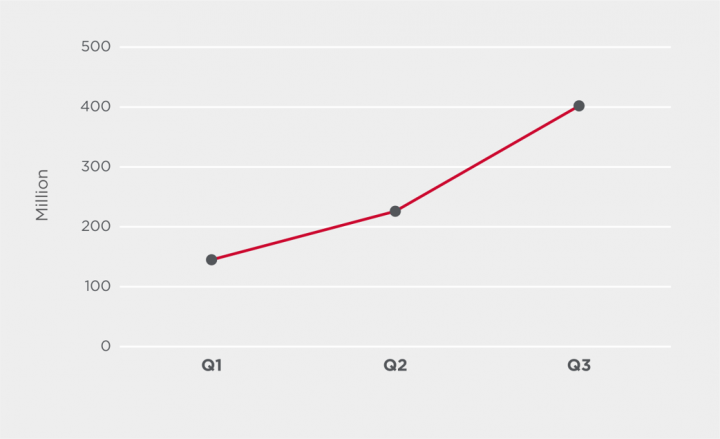
Average Internet of Things attacks per day
The average number of attacks against Symantec Internet of Things (IoT) honeypots* per day was down 8% in Q3 compared to Q2 2020. *Symantec IoT honeypots emulate protocols used by virtually all IoT devices, such as routers, connected cameras, digital video recorders, and so on.
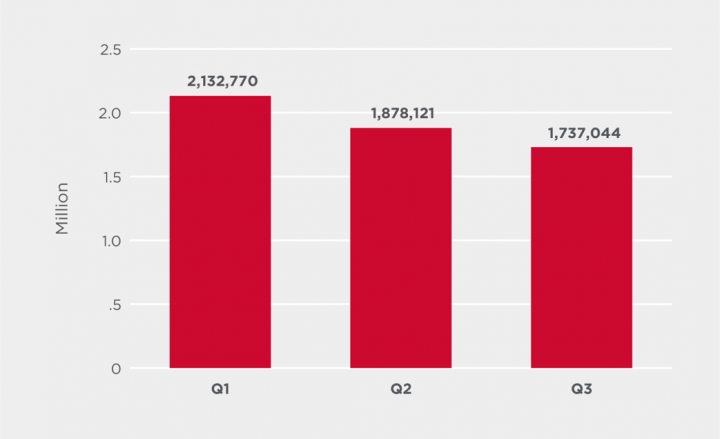
Unique IP addresses performing IoT attacks
While the number of attacks decreased, the number of unique IP addresses performing IoT attacks increased in Q3, up 18% over the previous quarter. This suggests that the botnets carrying out the attacks are increasing in size.
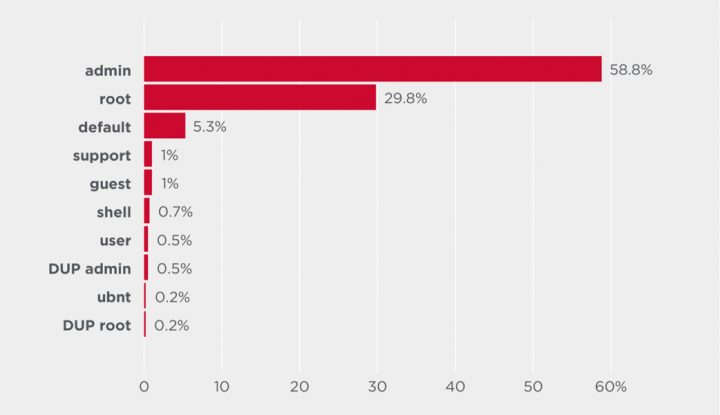
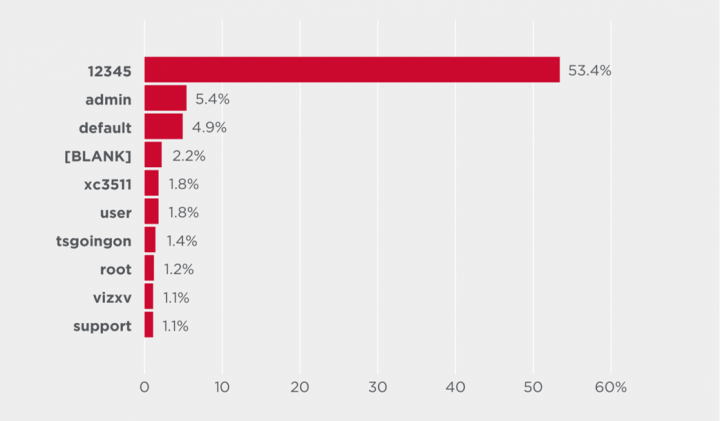
Top user names and passwords
The top ten user names and passwords used in attacks on IoT devices. Most of the credentials used by attackers are default or easily guessable.
Attack origination
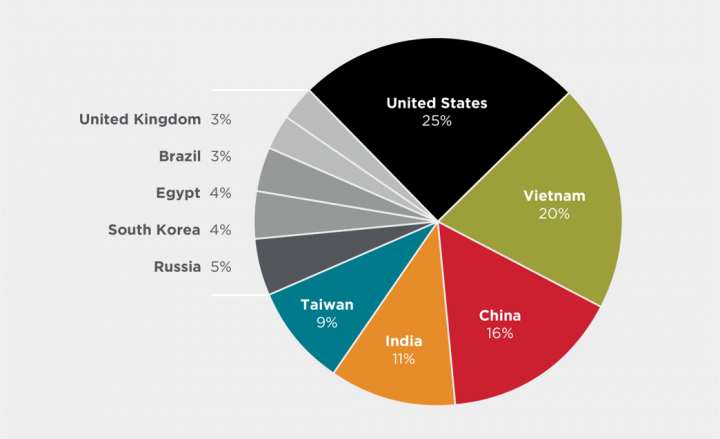
The largest number of attacks originated from IP addresses located in the U.S. with 25% of attacks emanating from here. However, the number of attacks originating in the U.S. decreased in Q3, down from 34% the previous quarter. The second highest number of attacks originated in Vietnam, followed by China, India, and Taiwan. Since attacks are carried out by botnets of infected IoT devices, these regions have the highest number of infected IoT devices.








We encourage you to share your thoughts on your favorite social platform.