Latest Intelligence for March 2018
The Inception Framework espionage group has been active and hiding in plain sight for three years, the email malware rate increases again, and browser-based coin mining without a browser emerges.
Some of the key takeaways from March’s Latest Intelligence, and the threat landscape in general, include an insight into what the Inception Framework group has been up to for the past three years, the email malware rate increases for the second month in a row, and malware that conducts browser-based cryptocurrency mining without a browser.
Malware
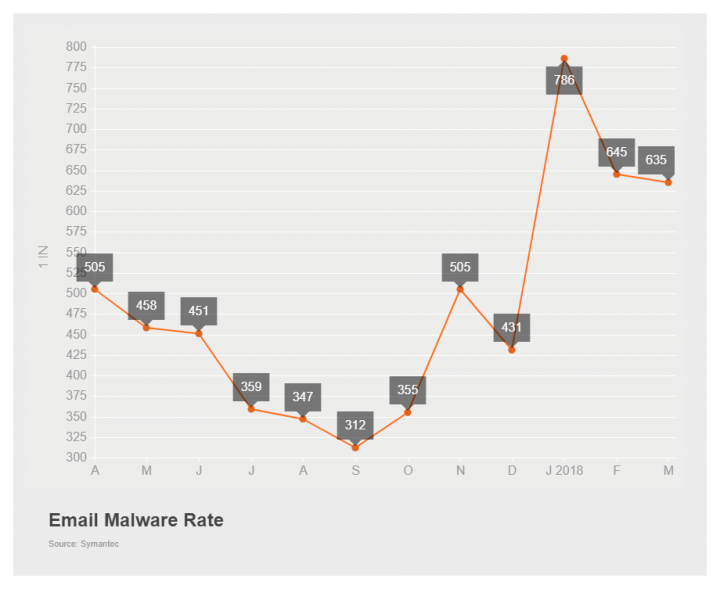
Following a significant drop in January (1 in 786 emails, down from 1 in 431 the previous month), the email malware rate rose in February and that increase continued into March. However, the increase was slight, up to 1 in 635 emails, compared to 1 in 645 for February. The Mining sector continued to have the highest email malware rate, increasing from 1 in 461 emails in February to 1 in 308 for March.
In March, Symantec discovered a new cryptocurrency mining malware (Trojan.Coinminer). However, this malware is not like most coinminers—it uses an interesting technique involving browser-based coin mining without any visible signs of a browser being used. One advantage of this type of threat for attackers is that coin mining may not be suspected for any CPU slowdown and instead the user may blame installed software for the problem.
Phishing
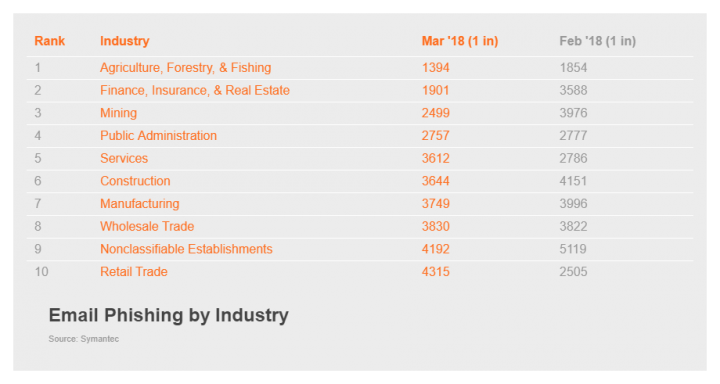
There was an increase in the rate of phishing emails in March, up from 1 in 3,331 emails in February to 1 in 2,981 in March. Agriculture, Forestry, & Fishing was the sector with the highest rate in March, with 1 in 1,394 received emails being a phishing attempt.
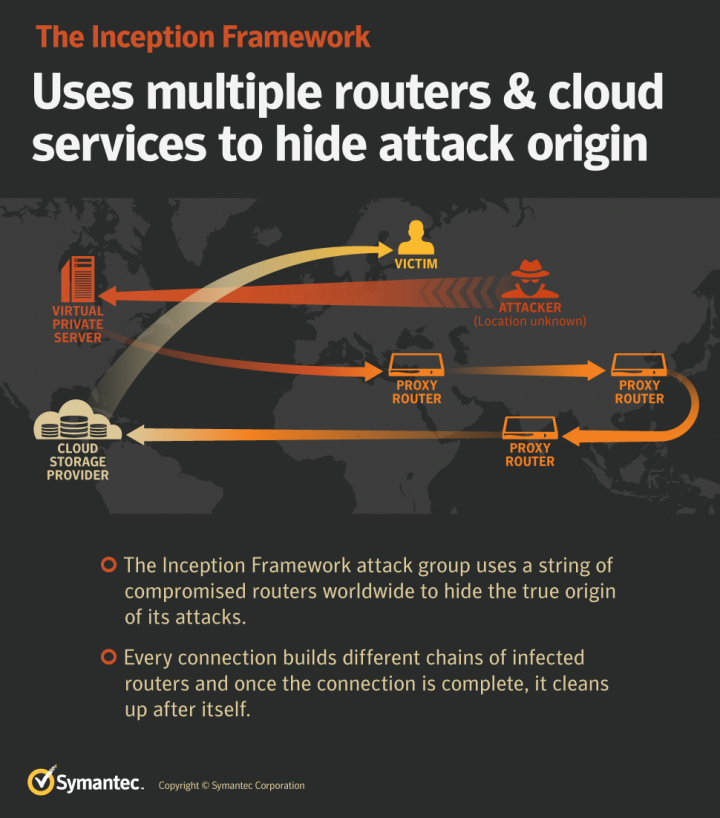
The cyber espionage group known as Inception Framework is using new types of lure documents in its spear-phishing campaigns and its malware has expanded to use new types of plugins, according to research published by Symantec in March. The group has remained active over the past three years, using cloud and the Internet of Things (IoT) to hide in plain sight. The group has been targeting organizations on several continents since 2014. It was first exposed by Blue Coat (now part of Symantec) in December 2014 targeting the Energy and Defense sectors, and organizations in the Consultancy/Security, Aerospace, Research, and Media sectors, in addition to embassies. However, the group appeared to fall quiet in late 2014 only to return in April 2015. Symantec has kept a close eye on the group’s activities, including changes in targeted regions.
Mobile
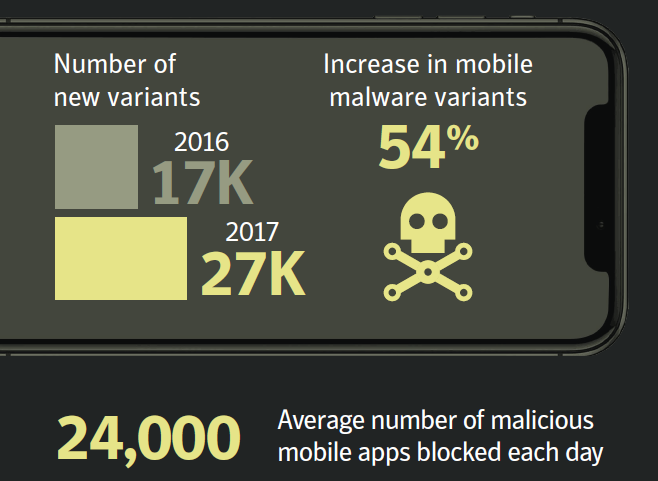
While there were no new Android malware families discovered in March, the threat to mobile devices is still as serious as ever. This is highlighted in this year’s ISTR (volume 23), which shows that new mobile malware variants increased by 54 percent in 2017, and an average of 24,000 malicious mobile applications were blocked by Symantec every single day.
Social media
Whenever there’s an event that generates interest online it’s inevitable that there will be scams trying to take advantage of the social media engagement that follows. This year’s Oscars ceremony was no exception and it wasn’t long before bots began targeting the Twitter accounts of award winners in order to spread gift card spam campaigns. The bots created fake accounts with similar handles to the real celebrities’ accounts. They then began replying to tweets in the real celebrities’ feeds. These replies contained spam links and were upvoted by other bot accounts so that the maximum number of people would see them.
This is just a snapshot of the news for the month. Check out the Latest Intelligence for the big picture of the threat landscape with more charts, tables, and analysis.






We encourage you to share your thoughts on your favorite social platform.